The United States Naval Research Laboratory (NRL) developed “The Onion Routing Protocol” (Tor) to securely relay intelligence online via layered encryption. This tutorial demonstrates how to build a Tor-Bridge relay with a Raspberry Pi 2, which is essentially a decentralized node relaying a constituent layer of encrypted-data that is ultimately combined with the entire layer of data processed in part with other Tor-nodes, or “bridges” on the network. According to the official Tor website, the lack of security on the Internet and its ability to be used for tracking and surveillance was already abundantly clear as far back as 1995, so the NRL sought to create Internet connections that don’t reveal identities, even to someone or some entity monitoring the network. They pioneered the first prototypes of onion-routing. If you would like to know more about the details of Tor and how it works from an elementary perspective, check out this post: “How Does Tor Work?”
Essentially, Tor is a network of three types of node-relays as defined by the Tor Community Docs:
- Non-Exit Relay: A guard or middle-relay (aka non-exist relays) are the first relay in the chain of 3 relays building a Tor-circuit. A middle relay is neither a guard nor an exit relay, but acts as the second hop between the two. To become a guard, a relay has to be stable and fast (at least 2MByte/s) otherwise it will remain a middle relay.
- Exit Relay: The exit relay is the final relay in a Tor circuit, the one that sends traffic out its destination. The services Tor clients are connecting to (website, chat service, email provider, etc) will see the IP address of the exit relay instead of their real IP address of the Tor user; Exit relays have the greatest legal exposure and liability of all the relays– so this tutorial will part ways with you here at that trail to read more about Exit Relay at Tor but we will leave you to safely and legally build a Tor Bridge-Relay as defined below 🙂
- Bridge Relay: Tor bridges are nodes in the Tor-network that are not listed in the public Tor directory, which make it harder for ISPs and governments to block them. Bridges are useful for Tor users under oppressive regimes (ie China and Iran) or for people who want an extra layer of security because they’re worried somebody will recognize that they are contacting a public Tor relay IP address. Bridges are a great option if you can only run a Tor node from your home network, have only one static IP, and don’t have a huge amount of bandwidth to donate; we recommend giving your bridge at least 1 Mbit/sec- every Tor Bridge counts! If you want to help make the world more securely-connected, please proceed as instructed and build a Tor Bridge!

Parts List
- Raspberry Pi 2 (or greater)
- 16 GB SanDisk MicroSD
- Mouse and Keyboard
- HDMI Monitor
- CAT-5/6E Cable
- MicroSD Formatter
Installing Tor
Initially, I began experimenting with Tor Bridge as documented after this heading Debian/Ubuntu Server (18.04). Although I succeeded with that approach, it was much more time-consuming than my first time experimenting with KALI-LINUX– so it’s recommended to proceed with the latter as detailed below if running a Tor Bridge.
Download KALI-LINUX for Raspberry Pi Install
- Go to Offensive Security and download go to Offensive Security and select “Raspberry Pi” (scroll-down the page and click on link “Raspberry Pi” for the drop-down menu and download the compressed .img file (non-64-bit) for Raspberry Pi 2,3,4; please note, you can also proceed below with Ubuntu Server if so inclined).
- Download The Unarchiver tool (available for free download at the Apple App Store) to unpack the image file “kali-linux-2019.3a-rpi3-nexmon.img.xz” so it formats to “kali-linux-2019.3a-rpi3-nexmon.img” to burn on the Samsung MicroSDXC.
- Input Samsung EVO-select MicroSDXC to dock and connect to computer via USB; download the appropriate SD-card formatter compatible with your OS to prepare this tutorial at the SD association OR you can use the Disk Utility tool in macOS Mojave- format Samsung MicroSDXC for FAT-32.
- Burning the unarchived KALI-LINUX Raspberry Pi 3 image-file (n00bs- download and use the balenaEtcher tool).
- Raspberry Pi 2 image-file (n00bs- download and use the balenaEtcher tool).
- Insert SSD into Raspberry Pi 2
- For Power-Users:
diskutil listsudo diskutil unmount /dev/your-SANDISK-BOOT-Identifier(egsudo diskutil unmount /dev/disk4s1).sudo dd bs=1m if=kali-linux-2019.3a-rpi3-nexmon.img.xzof=/dev/disk4 conv=sync- You can use the shortcut Ctrl + T to check the progress of the write process.
- If you’re unfamiliar with command-line syntax, check-out explainshell.com and copy/paste the commands herein to understand what they execute.
Prepare Raspberry Pi for KALI-LINUX Install
- Insert SSD containing burned Ubuntu Server ISO-file into Raspberry Pi.
- Turn-on Raspberry Pi.
- After configuring Raspberry Pi user-authentication credentials, run the following commands to update the the Ubuntu Server environment (default KALI-LINUX username is “root” and default password is “toor”; you will be prompted to enter a new password).
sudo apt-get update.sudo apt-get upgrade.sudo reboot.- For the sake of InfoSec, set-up an easy firewall for the Raspberry Pi 2 in Ubuntu Server by running
sudo apt install ufw, followed by the sequence of commands below:sudo ufw allow 3443 comment "TOR-circuit"sudo ufw allow 3480 comment "TOR"sudo ufw enable- Then recommend rebooting with
sudo reboot
- Lastly, you can skip this step if you don’t plan to remotely access this device on your network, but may be a good idea to prepare just in case:
- Run
ifconfig -ato list the host-IP address. sudo apt-get install openssh-serversudo ufw allow 22sudo reboot
- Run
- After running the above commands here in step-8 and then rebooting, you will have the option to remotely access this Raspberry Pi 2 from another computer on network, which will be required if you’re unable to synchronize your full-node by limiting the memory-cache on-board; basically, you will be forced to download and run a full-node briefly on another computer attached to your network and after a complete download, secure copying it from one terminal to another- please proceed to secure copy below if that becomes the case.
- Next, secure root-access by running
sudo passwd rootand then type a new password (please note you will now use this as the username “root” as the designated username along with its password to be entered). - Next type
exitand hit the Return-key; then log-in using “root” as the username and the corresponding password entered. - Lastly recommended mod is to rename the host/device home-name by running the following command according to the syntax:
usermod -l -d /home/ -morsudo usermod -l newUsername oldUsernameand changing the host/device name to an identifiable name to easily access on-network by running (e.g.)sudo hostnamectl set-hostname raspberrypi2.
Installing Tor on KALI-LINUX
After starting the Raspberry Pi 2 with KALI-LINUX, simply install Tor with the one-liner as explained within the Tor community-docs: sudo apt-get install tor. After the install, proceed exactly as outlined below within previously mentioned Tor-docs:
sudo apt-get install obfs4proxy- Access both of these Tor-services options and set
NoNewPrivileges=no– be sure to save these files by hitting the ESC-key + x to write/save the service-options.vi /lib/systemd/system/tor@default.servicevi /lib/systemd/system/tor@.service- Then run
systemctl daemon-reloadsystemctl restart tor.
- Skip this step if you choose a port smaller than 443 for port-forwarding:
- If running another port besides smaller than 1024 (like 443), you must assign obfs4 binding capability to that port by running (if you’re following this tutorial, run it):
sudo setcap cap_net_bind_service=+ep /usr/bin/obfs4proxy. If you need to unbind the port for whatever reason in the future, simply runsudo setcap cap_net_bind_service=-ep /usr/bin/obfs4proxy.
- If running another port besides smaller than 1024 (like 443), you must assign obfs4 binding capability to that port by running (if you’re following this tutorial, run it):
- Run vi Modify your torrc-file according to the below markdown:
RunAsDaemon 1
BridgeRelay 1
Log notice file /var/log/tor/notices.log
Log debug file /var/log/tor/debug.log
Log notice syslog
Log debug stderr
ORPort 3443
ServerTransportPlugin obfs4 exec /usr/bin/obfs4proxy
ServerTransportListenAddr obfs4 0.0.0.0:3448
ExtORPort auto
## If you know to set-up DynamicDNS, uncomment the line below
## Address your-dyanmic-dns
Nickname SatoshiNakamoto
SatoshiNakamoto <0xc78e9d242552d5da800a87b588dc3d2024a9fa0f@ethmail.cc>
RelayBandwidthBurst 200 KB # But allow bursts up to 200KB/s (1600Kbps)
ExitPolicy reject *:*
PublishServerDescriptor 0Download Ubuntu Server for Raspberry Pi
- Go to Ubuntu and download Ubuntu Server for Raspberry Pi 2 (scroll-down the page and click on link “Ubuntu Server image for Raspberry Pi 2″; please note, you can also proceed with a Raspbery Pi 2 with Ubuntu Server if so inclined).
- Download The Unarchiver tool (available for free download at the Apple App Store) to unpack the image file “ubuntu-18.04.3-preinstalled-server-arm64+raspi2.img.xz” so it formats to “ubuntu-18.04.3-preinstalled-server-armhf+raspi2.img” to burn on the Samsung MicroSDXC.
- Input Samsung EVO-select MicroSDXC to dock and connect to computer via USB; download the appropriate SD-card formatter compatible with your OS to prepare this tutorial at the SD association OR you can use the Disk Utility tool in macOS Mojave- format Samsung MicroSDXC for FAT-32.
- Burning the unarchived Ubuntu Raspberry Pi 2 image-file (n00bs- download and use the balenaEtcher tool).
- Insert SSD into Raspberry Pi 2
- For Power-Users:
diskutil listsudo diskutil unmount /dev/your-SANDISK-BOOT-Identifier(egsudo diskutil unmount /dev/disk4s1).sudo dd bs=1m if=ubuntu-18.04.3-preinstalled-server-armhf+raspi2.imgof=/dev/disk4 conv=sync- You can use the shortcut Ctrl + T to check the progress of the write process.
- If you’re unfamiliar with command-line syntax, check-out explainshell.com and copy/paste the commands herein to understand what they execute.
Prepare Raspberry Pi for Ubuntu Server Install
- Insert SSD containing burned Ubuntu Server ISO-file into Raspberry Pi.
- Turn-on Raspberry Pi.
- After configuring Raspberry Pi user-authentication credentials, run the following commands to update the the Ubuntu Server environment (default Ubuntu Server username is “ubuntu” and default password is “ubuntu”; you will be prompted to enter a new password).
sudo apt-get update.sudo apt-get upgrade.sudo reboot.- For the sake of InfoSec, set-up an easy firewall for the Raspberry Pi 2 in Ubuntu Server by running
sudo apt install ufw, followed by the sequence of commands below:sudo ufw allow 3443 comment "TOR-circuit"sudo ufw allow 3480 comment "TOR"sudo ufw enable- Then recommend rebooting with
sudo reboot
- Lastly, you can skip this step if you don’t plan to remotely access this device on your network, but may be a good idea to prepare just in case:
- Run
ifconfig -ato list the host-IP address. sudo apt-get install openssh-serversudo ufw allow 22sudo reboot
- Run
- After running the above commands here in step-8 and then rebooting, you will have the option to remotely access this Raspberry Pi 2 from another computer on network, which will be required if you’re unable to synchronize your full-node by limiting the memory-cache on-board; basically, you will be forced to download and run a full-node briefly on another computer attached to your network and after a complete download, secure copying it from one terminal to another- please proceed to secure copy below if that becomes the case.
- Next, secure root-access by running
sudo passwd rootand then type a new password (please note you will now use this as the username “root” as the designated username along with its password to be entered). - Next type
exitand hit the Return-key; then log-in using “root” as the username and the corresponding password entered. - Lastly recommended mod is to rename the host/device home-name by running the following command according to the syntax:
usermod -l -d /home/ -morsudo usermod -l newUsername oldUsernameand changing the host/device name to an identifiable name to easily access on-network by running (e.g.)sudo hostnamectl set-hostname raspberrypi2. sudo reboot
Debian/Ubuntu Server (18.04 Bionic Beaver)
- After rebooting the Raspberry Pi, you may begin the install of Tor for the Debian-stable by running
sudo-get install tor; you might also consider install Xubuntu to access this tutorial via FireFox or the Tor Docs because the commands below are quite long- to do, simply runsudo apt-get install xubuntu-desktopand thensudo reboot. - Per the Tor Docs, there are a few modifications required; first proceed with the following steps configured as “Debian Bionic Beaver (18.04 LTS)” for Tor Stable:
- Run
deb https://deb.torproject.org/torproject.org bionic main. - Next, run
deb-src https://deb.torproject.org/torproject.org bionic main. - Then add the gpg-keys used to sign the packages running the following commands:
curl https://deb.torproject.org/torproject.org/A3C4F0F979CAA22CDBA8F512EE8CBC9E886DDD89.asc | gpg --import # gpg --export A3C4F0F979CAA22CDBA8F512EE8CBC9E886DDD89 | apt-key add -- After assigning the gpg-keys, update with
sudo apt-get updatefollowed-byapt install tor deb.torproject.org-keyring.
- Run
- For this Debian/Ubuntu-build, run
sudo apt-get install obfs4proxy - Access the Tor-configuration-file by running
vi /etc/tor/torrc; input the following parameters by uncommenting or inputting where appropriate:RunAsDaemon 1ORPort 3443ServerTransportPlugin obfs4 exec /usr/bin/obfs4proxy.ServerTransportListenAddr obfs4 0.0.0.0:3448- Uncomment line
ExtORPort auto. Nickname choose-whatever-you-wantContactInfo your-contact-name <your-email-address@whatever.com>- eg
SatoshiNakamoto <0xc78e9d242552d5da800a87b588dc3d2024a9fa0f@ethmail.cc>
- eg
- Hit ESC-key + x to save and exit vim.
- If running another port besides 9901 (like 443), you must assign obfs4 binding capability to that port by running (if you’re following this tutorial, run it):
sudo setcap cap_net_bind_service=+ep /usr/bin/obfs4proxy. If you need to unbind the port for whatever reason in the future, simply runsudo setcap cap_net_bind_service=-ep /usr/bin/obfs4proxy. - Access both of these Tor-services options and set
NoNewPrivileges=no– be sure to save these files by hitting the ESC-key + x to write/save the service-options.vi /lib/systemd/system/tor@default.servicevi /lib/systemd/system/tor@.service- Then run
systemctl daemon-reloadsystemctl restart tor.
- Restart the Raspberry Pi by running
sudo reboot - Tor should automatically start loading by running
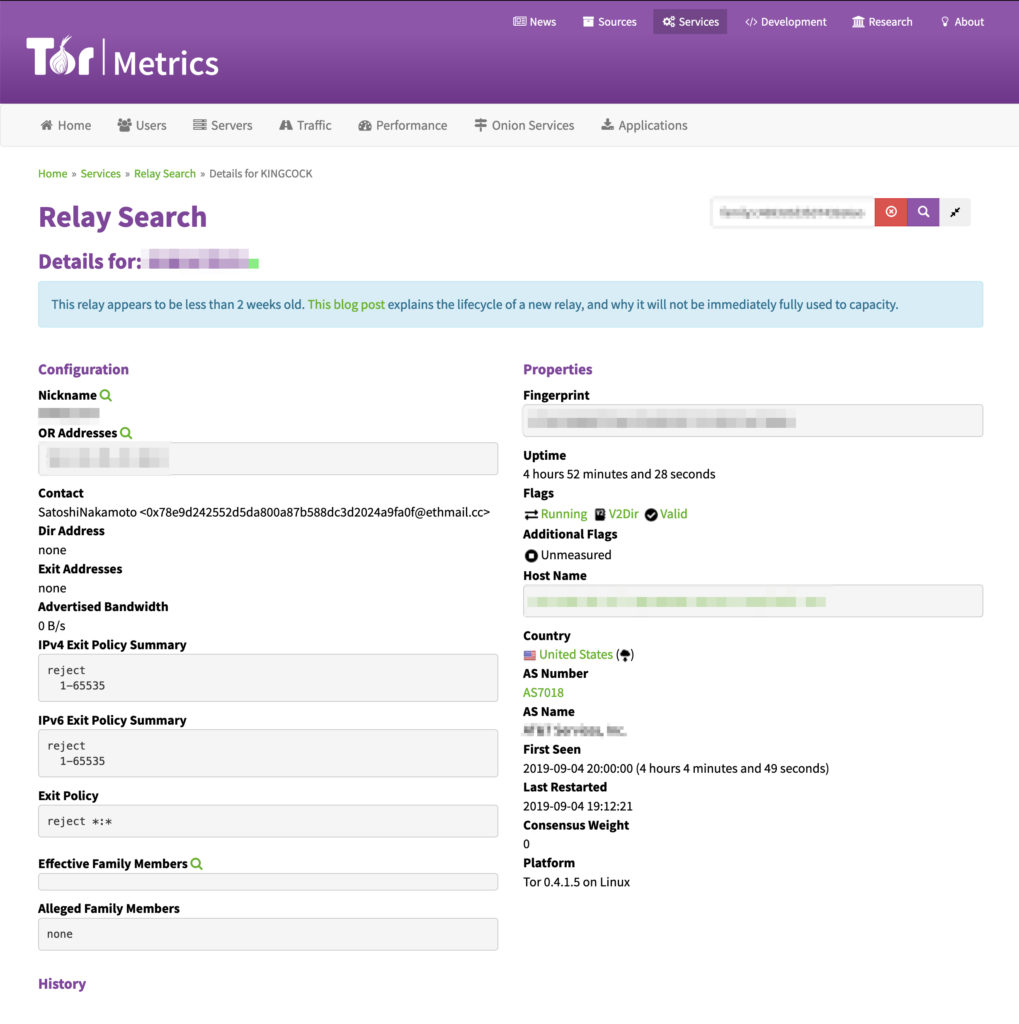
/var/logand thencat syslogORcd /var/log/tor/thencat logto verify Tor-connection status, or check out Tor Atlas to verify a successful connection and network status; if you’re running a Tor Bridge, you must search for the hashed-fingerprint within the “Advanced Search” tab, which can be found within the “notices.log” file located within/var/log/tordirectory- simply runcat notices.logand the returned terminal-output should contain a hashed-fingerprint value that can be retrieved on Tor Atlas, as depicted by the below screenshot. - Please Note: For all concerns about legal matters and safety, the Tor config-file as detailed above by default sets the
ExitRelay Policy to 0– so unless you specifically addExitRelay 1within the torrc config-file, Tor will automatically run as a Bridge Relay instead of an Exit Relay as disclaimed within the notices.log file after running starting Tor and within their documentation as of 09/05/2019; you can also uncomment lineExitPolicy reject *:*within the torrc config-file just to err on the side of caution to ensure your node is a Bridge Relay. The best way to confirm your Tor-node Exit Policy is verify with Tor Atlas, as depicted by the below screenshot.
Optimizing Tor Bridge
Recap: torrc
To recap, a legally compliant Tor Bridge will includeExitPolicy reject *:*ExitRelay 1 anywhere whatsoever in the config-file; an example of a USA legally-compliant Tor Bridge torrc config-file is provided within the below markdown:
RunAsDaemon 1
BridgeRelay 1
Log notice file /var/log/tor/notices.log
Log debug file /var/log/tor/debug.log
ORPort 3443
ServerTransportPlugin obfs4 exec /usr/bin/obfs4proxy
ServerTransportListenAddr obfs4 0.0.0.0:3448
ExtORPort auto
## If you know to set-up DynamicDNS, uncomment the line below
## Address your-dyanmic-dns
Nickname SatoshiNakamoto
SatoshiNakamoto <0xc78e9d242552d5da800a87b588dc3d2024a9fa0f@ethmail.cc>
RelayBandwidthBurst 200 KB # But allow bursts up to 200KB/s (1600Kbps)
ExitPolicy reject *:*
PublishServerDescriptor 0Other Helpful Tips
Get comfortable monitoring your Tor Bridge install by running the following within their respective directories:
- For /var/log/tor/notices.log:
tail -f -n -100 notices.log - For /var/log/syslog:
`tail -f -n -100 syslog
Also, if you prefer to avoid loading Xubuntu upon restart to conserve RAM, type CTRL + ALT + F3 at the Xubuntu welcome screen.